Joshua Lee
Allen ISD STEAM Center
Advanced Computer Science II
David Ben-Yaakov
August 25, 2022
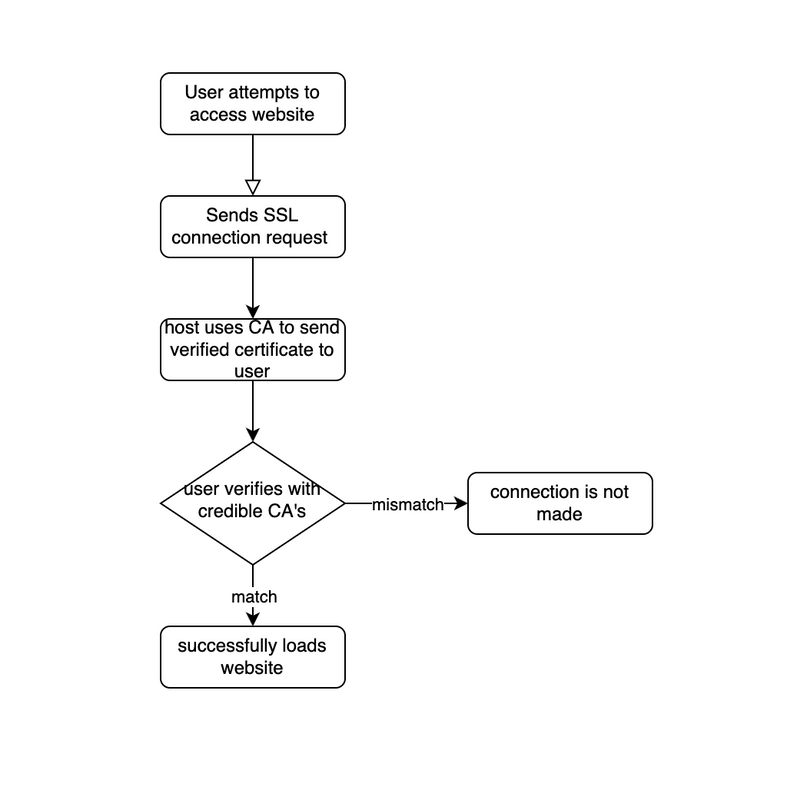
Gibson Research Corporation, 2020). The development of this new enhancement of user security and privacy came at a price during the early days of the Internet, so it was only used for sensitive information. However, as technology advanced and the cost of this new connection became more affordable, many websites switched from HTTP to HTTPS. A difference between HTTP and HTTPS was how HTTPS improved security through the implementation of "Certificate Authorities" (CA). CA's are organizations that check the legitimacy of webpages by verifying if the webpage was properly digitally signed by the owners. This transition led to the
Going Dark Problem, where organizations and schools were forced into searching for new ways to monitor and filter information. In response to this issue, they developed a new technology known as
HTTPS Proxy Appliances. This technology is a device that allows for organizations and schools to be between a user and their application, providing a bypass through the unbreakable security and privacy of HTTPS connections.
HTTPS Proxy Appliances, there are MITM's (
man-in-the-middle). MITM presents risks to an MITM attack, which is
when a perpetrator positions himself in a conversation between a user and an applicationin order to eavesdrop or impersonate the user (Imperva, 2019). Almost like a version of MITM, SSL interceptions cannot be prevented directly. However, they can be reliably detected as impossible to completely spoof a security certificate, so they can be resolved rather than prevented. SSL interceptions are reliably detected by verifying the fingerprint of the certificate, as any alterations to the certificate will result in the creation of a new fingerprint/cryptographic hash.
hash?. Computer Science Stack Exchange. Retrieved August 24, 2022, from
